Hello, Waves Community! I’d like to discuss some thoughts on the different ways to implement 2FA (Two Factor Authentication) for the Waves platform. We have lots of ideas about how to develop this feature, and I want to know your opinions about this important step.
Before I give you a few details about each of the different approaches, I want to explain the difference between the login processes in centralized and decentralized applications. If you already know this, skip to the section “2FA with the Waves Mobile App”.
INTRODUCTION
In centralized platforms, an individual gains access to an application by authenticating themselves using their username or email address, with a password.
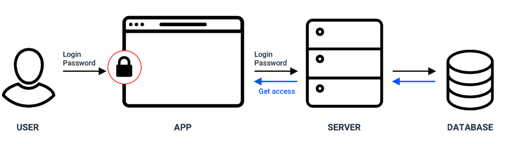
After logging in, the user has full control and can carry out any transaction.
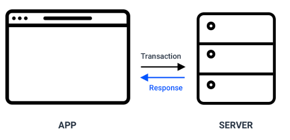
Decentralized applications do not store any user login data. Anybody can see all the information on the blockchain.
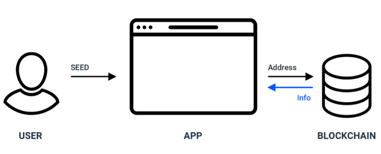
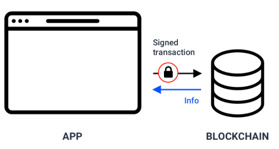
When a user submits a transaction, he signs it with his private key and the blockchain validates it. Everything works through cryptography.
Centralized apps are like a house where the door is locked and when you open the lock, you can take out anything you want. Decentralized apps are like a house where there is no door, but you can take out only your own possessions.
Thus, in applications based on the blockchain, it is possible to protect either the SEED itself (hardware wallets already do this), or to protect a transaction - to add one more condition for its validity. That is, to convert the account into a multi-sig account, which is the essence of 2FA for decentralized applications.
Below I will describe various ways to approach this problem.
2FA WITH THE WAVES MOBILE APP
This method assumes that the account will be converted to a double-signature account. That is, to send the transaction it must be signed with two private keys. Both SEEDs are stored by the user. Either one is stored locally on the computer, and the second on a mobile phone, or both are stored on the mobile phone (but stored separately, and encoded by different passwords).
This method can be developed either with the current Waves mobile application or a with a new, separate one.
2FA set up
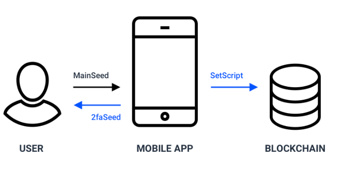
Create transaction
One of the ideas for how the different devices can be connected via the blockchain is the following:
If the user wants to send some tokens from his Desktop or Web Client, he fills in a Send form as usual, but a Data transaction is sent to the blockchain instead a Transfer transaction. This Data transaction contains all the information from the Send form.
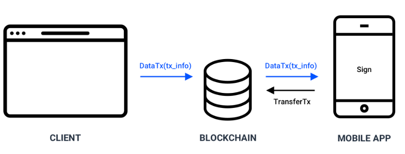
The Waves Mobile app will get this Data transaction from the blockchain and will display a window to confirm the transfer. If the user confirms it, the transfer transaction will be signed twice, with the main and 2fa SEEDs, and will be sent to the blockchain.
Pros and cons
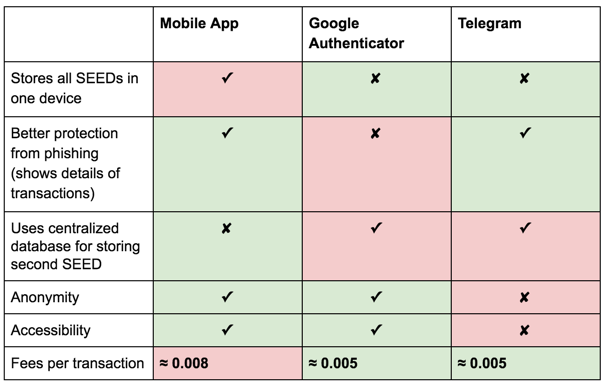
This method is pretty good because it’s decentralized, but users must pay an additional fee per Data transaction. Both SEEDs can be stored in one device.
2FA WITH GOOGLE AUTHENTICATOR
The basis of this method is that it does not store both SEEDs on the same device, in contrast to the previous way. But it requires some degree of centralization.
This method assumes that the account will be converted to a triple-signature account. Two SEEDs are stored by the user: one is stored locally with the second as backup (to be used only in a critical situation to reset 2FA), with the third one created and held on a server, encrypted by a server key and stored in a centralized database. The user never receives this SEED, and it is used only to sign transactions.
The user must download and set up Google Authenticator, using a secret key. The secret key has to be communicated to the server too.
2FA set up
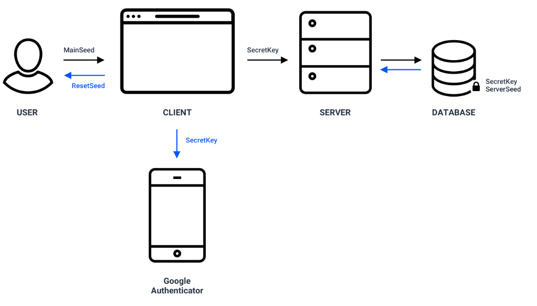
Create transaction
Every time the user wants to send a transaction, he signs it with his main private key and enters a one-time code from Google Authenticator. This code is sent to the server and if it is valid, the server signs the transaction too.
Pros and cons
This method is good because SEEDs are not stored in one device and Google Authenticator is popular among users. However, it needs a centralized database and it does not work in the case when a transaction has been replaced with fraudulent data.
2FA WITH TELEGRAM
This method is the same as the previous one in its architecture, but in place of Google Authenticator, the user employs his Telegram account.
Pros and cons
2FA with Telegram is better than 2FA with Google Authenticator in cases where transaction data has been replaced with fraudulent content, since a Telegram bot will show the transaction details. However, Telegram does not work stably in some countries.
COMPARISON
CONCLUSION
All methods have their pros and cons. What do you think about each of them? Maybe you have a good idea of your own, in which case feel free to write it in the comments.
What way is most convenient for you?
- The Current Waves Mobile app
- A new Waves Mobile app (Waves Authenticator)
- Google Authenticator
- Telegram
0 voters
